A. Brief Introduction
Usage:
Explicit Secure Channel initiation allows the off-card entity to instruct the card (EXTERNAL AUTHENTICATE COMMAND) as to what level of security is required for the current Secure Channel and apply this level of security to all the subsequent messages exchanged between the card and the off-card entity until the end of the session.
Flow:
 |
| Figure 1: Explicit Secure Channel initiation Flow |
B. Commands Structure
B.1 INITIALIZE UPDATE
 |
| Table 1: INITIALIZE UPDATE command structure |
Host challenge: randomly generated number
Response Message:
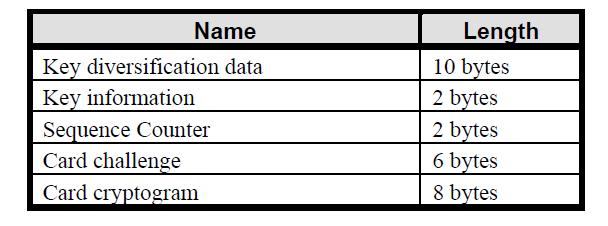 |
| Table 2: INITIALIZE UPDATE command Response Message |
B.2 EXTERNAL AUTHENTICATE
 |
| Table 3: EXTERNAL AUTHENTICATE command structure |
Host cryptogram: 8 bytes
MAC: 8 bytes
Security Level:
 |
| Table 4: Security Level coding |
C. Way to calculate authentication cryptogram and CMAC
Way to calculate Host authentication cryptogram and CMAC will be illustrated by example below:
8050000008659CFAB838A36C9E SW611C
00C000001CSW00000000000000000000FF02000092F744482D1E 26A365DF89B1EAEA9000
8482000010448126B770B27702D770D0A0001B05AASW9000
1. Generate Session Key
 |
| Figure 2: Session Key generation diagram |
constant for R-MAC: '0102'
constant for S-ENC: '0182'
constant for DEK: '0181'
*Sequence counter - get it from response of INITIALIZE UPDATE command. refer to Table 2.
*CBC encryption: Triple DES in CBC mode, ICV: 0000000000000000
base key used(Depends on your implementation.Not a fixed value):
ENC: 30313233435363738393A3B3C3D3E3F
MAC: 404142434445464748494A4B4C4D4E4F
DEK: 505152535455565758595A5B5C5D5E5F
a. generate S-ENC:
Derivation data: 01820000000000000000000000000000
S-ENC: 8D04904F18B948EEB78A1972B9527E71
b. generate S-MAC:
Derivation data: 01010000000000000000000000000000
S-MAC: D1C28C601652A4770D67AD82D2D2E1C4
2. Calculate Host Authentication Cryptogram
a. Concatenated data: Sequence Counter+Card Challenge+Host Challenge
Concatenated data: 000092F744482D1E659CFAB838A36C9E
b. Apply DES padding:
- Append an '80' to the right of the data block;
- If resultant data block is a multiple of 8 bytes, no further padding is required;
- Append binary zeroes to the right of the data block until the data block length is a multiple of 8 bytes.
* If data is being padded with the intention of generating a MAC, the padding is discarded following the DES operation.
Padding data: 000092F744482D1E659CFAB838A36C9E8000000000000000
c. Generate authentication cryptogram by using signature method.
Signature method: Full Triple DES, more specified: Triple DES in CBC mode, , ICV: 0000000000000000
Since K = K', Algorithm 3 is downgrade to Algorithm 1. So it is TDES in CBC mode.
After encrypt: B84449ADC4325C5BF9366187E977797D448126B770B27702
Host cryptogram will be the last 8 bytes.
Host cryptogram: 448126B770B27702
*Way to calculate Card authentication cryptogram is same as above. The only different is the concatenated data. Concatenated data: Host Challenge+Sequence Counter+Card Challenge.
b. Padded data: 8482000010448126B770B27702800000
c. C-MAC generation use Single DES Plus Final Triple DES (so called Retail MAC). Refer to Figure 3 below:
Key 1: D1C28C601652A477
Key 2: 0D67AD82D2D2E1C4
Calculated CMAC: D770D0A0001B05AA
c. Generate authentication cryptogram by using signature method.
Signature method: Full Triple DES, more specified: Triple DES in CBC mode, , ICV: 0000000000000000
Since K = K', Algorithm 3 is downgrade to Algorithm 1. So it is TDES in CBC mode.
After encrypt: B84449ADC4325C5BF9366187E977797D448126B770B27702
Host cryptogram will be the last 8 bytes.
Host cryptogram: 448126B770B27702
*Way to calculate Card authentication cryptogram is same as above. The only different is the concatenated data. Concatenated data: Host Challenge+Sequence Counter+Card Challenge.
3. Calculate C-MAC
a. Organise your APDU command: 8482000010448126B770B27702b. Padded data: 8482000010448126B770B27702800000
c. C-MAC generation use Single DES Plus Final Triple DES (so called Retail MAC). Refer to Figure 3 below:
Key 1: D1C28C601652A477
Key 2: 0D67AD82D2D2E1C4
 |
| Retail MAC diagram |
Great Article. Helped me a lot to understand basic how things happen in Mutual Authentication.
ReplyDeleteNeed some more clarity. I am done with this mutual authentication step. Now Trying to fire delete command. Could you please help me how to create Wrapped command and next MAC for delete command
Thanks for the post it helped me a lot?
ReplyDeleteBut I didn't really understand the "Retail MAC diagram" and how to calculate C-MAC. Which one is the "Key 3" and which par of the result should we truncate ?